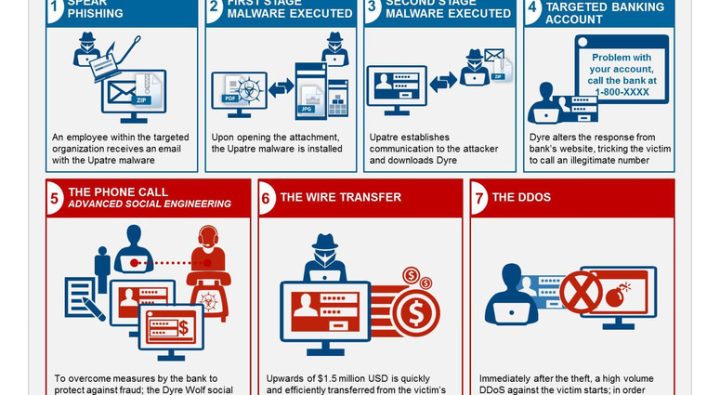
The evolution of a recent cyber-criminal threat illustrates how social engineering exploits the weakest link in data security
 Data security threats are constantly evolving to elude detection. A recent example, the Dyre Wolf campaign, highlights the use of social engineering techniques to obtain credentials and gain access to otherwise secure banking sites. People are the weakest link in any data security defense and Dyre Wolf illustrates perfectly why this is the case.
Data security threats are constantly evolving to elude detection. A recent example, the Dyre Wolf campaign, highlights the use of social engineering techniques to obtain credentials and gain access to otherwise secure banking sites. People are the weakest link in any data security defense and Dyre Wolf illustrates perfectly why this is the case.
What is Dyre Wolf?
Dyre wolf is an iteration of the Dyre malware that surfaced last year. Well-funded and organized cyber criminals recently used Dyre Wolf to steal more than $1 million from organizations that regularly transfer large sums between banks.
“This new strain is an example of malware in the wild, morphing into a threat that slips undetected past spyware and Antivirus programs,” stated Carl Mazzanti, CEO, eMazzanti Technologies. “Dyre Wolf is an unfortunate example of using social engineering to acquire account access credentials for the purpose of stealing large sums.”
How does it work?
Any businesses that transfer funds, and the banks where their accounts are located, are at risk. For an attack to be successful, a number of actions need to take place at the targeted enterprise.
- First, a user clicks on a phishing email to accept the malware package installation on their computer. Next, he uses that computer to access one of the hundreds of banking websites that Dyre is programed to monitor.
- At that point, the user will be redirected during logon to a FALSE bank web page that is bold enough to instruct the user to call a phone number and interact with a live operator.
- Once engaged, the operator collects the account credentials from the victim. This information is used to sign on and authenticate as the user and to later empty the account with a bank wire transfer to foreign accounts.
- A DDoS attack may follow to delay investigation of the theft.
Smaller banks and credit unions have been largely untouched by Dyre Wolf since the writers of the threat initially focused on larger targets. As the perpetrators earn money, we can be sure that their investments to increase the scope of banks and credit unions targeted will expand rapidly.
With few malware and spyware products detecting this strand of Dyre there are no current metrics that outline the extent of the infections. As Dyre can sit dormant for long periods of time, we must wait to see how many systems are infected and accounts compromised.
How does a business protect itself?
According to an April 3, 2015, article on ZDNet, security experts say that a comprehensive approach to address the human factor will best protect against the threat. They recommend that businesses:
- Train employees on security best practices and how to report suspicious activity.
- Consider conducting periodic mock-phishing exercises where employees receive emails or attachments that simulate malicious behavior. Metrics can be captured on how many potential incidents would have happened had the exercise been a real attack. Use these findings as a way to discuss the growing security threats with employees.
- Offer security training to employees to help understand threats and measures they can take to protect the organization.
- Provide regular reminders to employees on phishing and spam campaigns and that they shouldn’t open suspicious attachments or links from both work and personal emails.
- Train employees in charge of corporate banking to never provide banking credentials to anyone. The banks will never ask for this information.
How does a financial institution protect itself?
Some credit unions and banks have set up phone system announcements to educate customers that dial into their systems. Most likely, the writers of Dyre Wolf will not copy the complete auto attendant navigation trees in phone systems to trick inbound callers. To be safe, Banks and Credit Unions could educate their customer base to use a validation method only available to the bank through their auto attendant.
Another defense against the threat leverages mobile banking. When a patron calls in, the bank must verify a code sent to a mobile phone registered on the account to confirm the caller’s identity, and at the same time, that the bank is in fact the institution the patron thinks he or she is communicating with.
eMazzanti Can Help
Companies with inadequate data security are putting themselves at risk by increasing the likelihood of a successful Dyre Wolf or similar attack. They may suffer the costs of a security breach, including the loss of customer data, assets, revenue and reputation.
eMazzanti is ready to show business leaders how effective employee training combined with advanced data security technology will protect customer data and safeguard valuable business assets from Dyre Wolf attacks and other cyber-crime threats.
Strengthen network security and defend your business from loss of assets, revenue and reputation with eCare managed data security services. To explore the options, contact eMazzanti Technologies at info@emazzanti.net or call 1-866-EMAZZANTI.